IT Procurement for Identity Security and Counterfraud Solutions

Procuring the right identity and fraud prevention technologies is the difference between business as usual and a costly breach. Today’s enterprises must invest in identity security and counterfraud solutions to protect both their users and their data.
Are Verified Fans an Effective Way to Counter Ticket Scalping?

Ticket scalping continues to challenge the integrity of event access across sports, music and entertainment. “Verified Fan” programs to filter out bad actors before sales even begin. When integrated into a presale system, eIDV ensures that each code or link is tied to a verified individual—not just an account.
The Top 5 Ways to Improve Your Payments Security in 2025

As cybercriminals refine their tactics, financial institutions and businesses alike must aggressively evolve their security strategies. Protecting payment systems now demands a layered, client-centered, and analytics-driven approach.
How to secure yourself from credential stuffing account takeovers in 2025
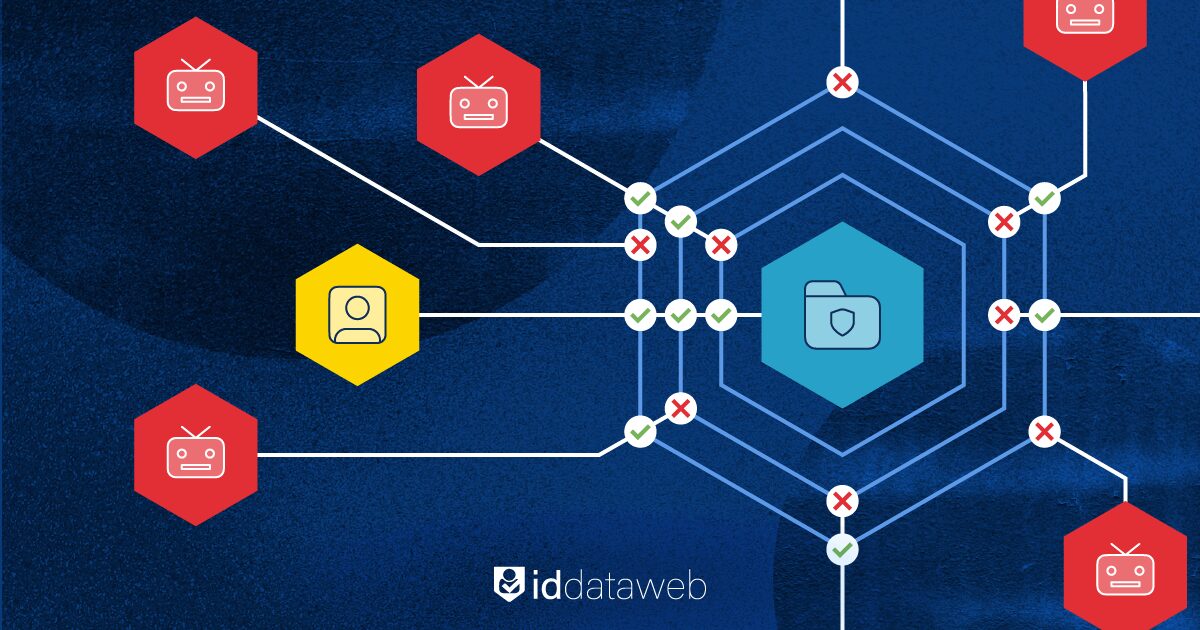
Credential stuffing flourishes where reused passwords meet static login flows. Using ID Dataweb’s millions of risk signals, security teams close that gap without frustrating customers.
How policy & decision engines counter account takeover fraud
Businesses that rely on static fraud rules or isolated authentication checks risk account takeover attacks. Decision engines that leverage real-time risk signals allow organizations to battle new fraud tactics.
Top fraud prevention challenges for airlines in 2025

Airlines in 2025 operate in an environment where identity is the new security perimeter – protecting it is paramount for safety, trust, and profit. Passenger identity verification, loyalty fraud, ticketing scams, and insider risks are testing the industry’s resilience.
Understanding Third Party Risk In Identity Management

If a vendor’s credentials fall into the wrong hands, your network becomes an open door. Security professionals must manage third-party users with the same (or stricter) standards reserved for internal staff.
The Fraud Triangle – Internal Identity Risk and IAM as a Defense Strategy

The Fraud Triangle has three core elements: Pressure, Opportunity, and Rationalization. These factors create conditions that encourage individuals—whether employees or third-party partners—to commit fraud.
Identity Fraud’s Impact on the Insurance Industry

The insurance industry handles vast amounts of personal information and large financial transactions every day. Criminals use clever tactics to slip through verification processes. So, insurers must balance offering a smooth customer experience and ensuring that security checks are comprehensive enough to stop fraud.
How Identity Verification Solves Health Insurance Fraud Challenges

Health insurance fraud is one of the most complex problems in modern healthcare. It sneaks into billing systems, siphons financial resources, and creates mistrust among patients, providers, and insurers. It’s easy to frame health insurance fraud as a problem of catching “bad actors,” but the reality is more nuanced. This article explores five common fraud […]







