Automating Workforce Identity Management with an Orchestration Platform
If you’re an IT administrator, you know the pain of traditional workforce identity management. Provisioning accounts, verifying identities, handling contractors, disabling access for departures. Identity orchestration simplifies IAM.
The Critical Role of Identity Proofing for External Identities in Access Governance

Organizations today rely heavily on a mix of contractors, vendors, gig workers, franchisees, and partners. As a result, enterprises must rethink how to onboard external users swiftly, but with enough rigor protect sensitive systems and data.
5 IAM Trends to Watch in 2025
Five trends shaping IAM this year that enterprise security professionals and business leaders should watch closely.
The Fraud Triangle – Internal Identity Risk and IAM as a Defense Strategy

The Fraud Triangle has three core elements: Pressure, Opportunity, and Rationalization. These factors create conditions that encourage individuals—whether employees or third-party partners—to commit fraud.
The Security and UX Benefits of Step-Up Authentication
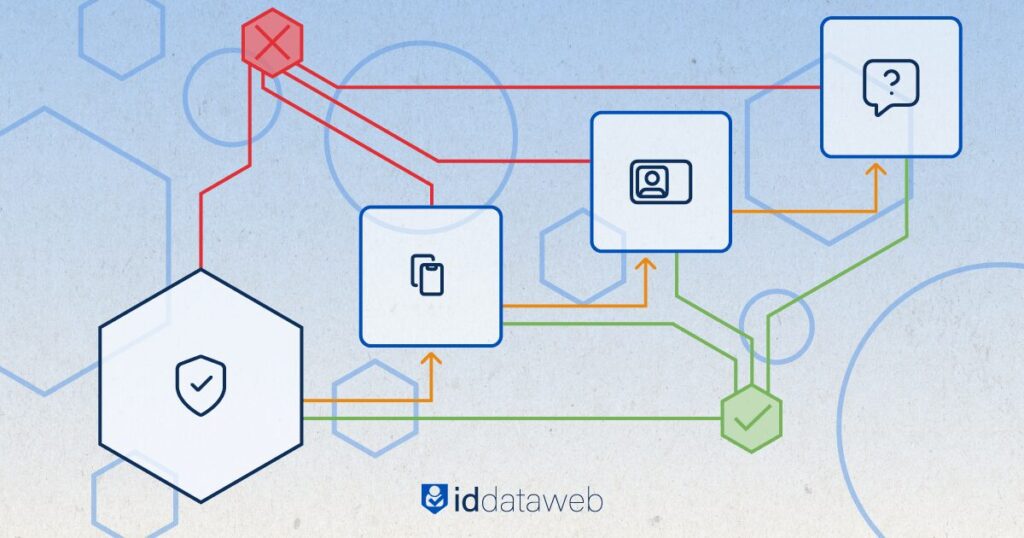
Step-up authentication tailors verification to the context of each interaction. The result is a powerful balance between low-friction for trusted users and strong security against suspicious activity fraudsters.
Just-In-Time Provisioning
An explainer on how the JIT principle from lean manufacturing has been adapted to identity provisioning solutions.







