Banks vs. Deepfakes: Protecting Customers from AI Voice Fraud

Unlike traditional robocalls, AI-generated voices sound natural. This guide explores how AI voice fraud exploits conventional call center security and how a multi-layered identity verification strategy can stop it.
Telecom Fraud Prevention: The Hidden Weak Link in Identity Security

Telecom fraud has become a major vector for identity-based attacks. Businesses treat phone numbers as unique identifiers, however, this approach fails to account for telecom based fraud.
Thwarting Modern Account Takeover Chains with Identity Threat Detection and Response
Modern enterprises, have invested in firewalls, encryption, and authentication. Yet call centers often remain a soft target. Agents have the authority to reset passwords and MFA. In modern account takeover (ATO) chains, identity—not credentials or firewalls—is the frontline.
A Guide to AI Fraud Detection in 2025

Artificial intelligence has unleashed a new wave of threats for enterprise cybersecurity teams. This article explores how adaptive authentication – particularly risk-based, step-up authentication – provides an effective countermeasure to AI-driven fraud.
Enterprise Call Center Procedures and Their Vulnerabilities to Identity‑Based Attacks
Call center procedures designed for customer convenience can be exploited by attackers to circumvent MFA and other guardrails. Here’s how identity-threat detection and risk mitigation secures the call center.
The Complete Guide to Document Verification
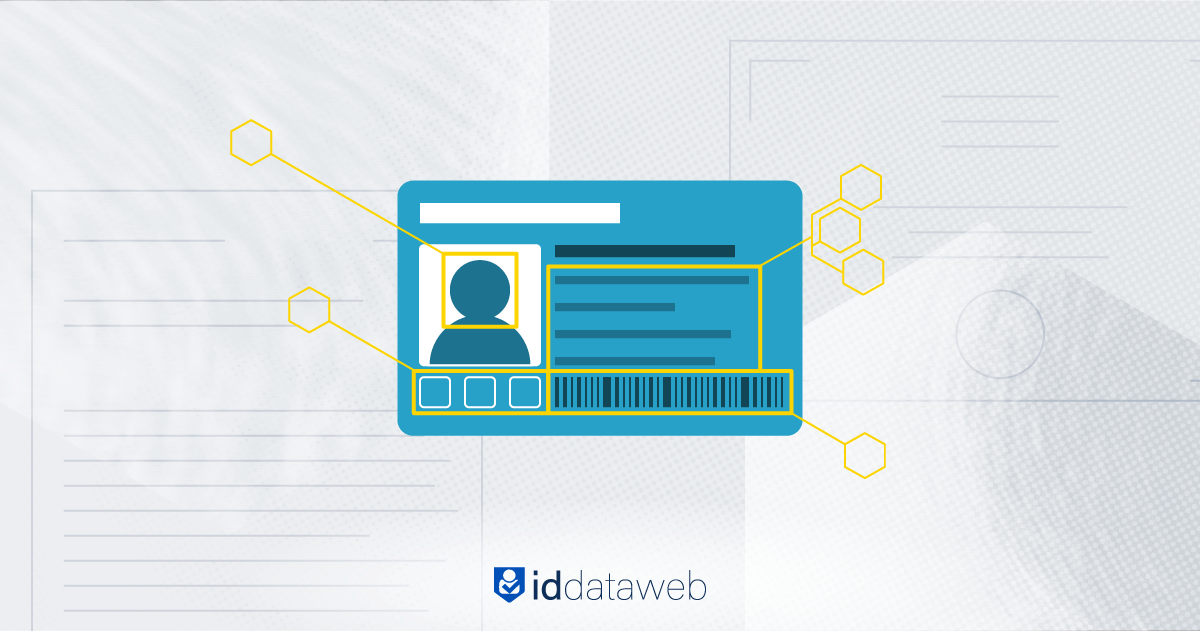
Document verification is a preventative control that mitigates account opening fraud. This guide will examine how it works, and explain how layered threat signals enhance document verification technologies.
Why Multi-Signal, Layered Identity Threat Detection is Key to Stopping Ticket Scalping

High-profile events in recent years have seen tickets sell out within seconds, leaving most fans empty-handed. This guide examines scalping operations ad how multi-signal, layered identity threat detection can restore access to legitimate buyers.
Recycled Phone Number Fraud & How Retired Lines Are Used in Account Takeovers

In the United States, around 35 million phone numbers are recycled each year. This article explores how recycled numbers enable account takeovers, then shows how ID Dataweb’s new MobileMatch risk signals address this issue.
How enterprises can secure MFA enrollment with identity verification and risk reduction workflows in 2025

Even as enterprises have broadly adopted MFA for their workforces, attackers are finding ways around it. Protecting against threats to secure MFA enrollment, requires stronger identity verification and adaptive risk-based workflows.
Beyond Device Fingerprinting: Orchestrating Device Risk Signals Into Every Access Decision

Device fingerprinting used to be sufficient. But with new privacy tools and account takeovers on the rise, security teams must supplement fingerprinting with broader signals to stop fraud.







