July 10th, 2024
By Matt Cochran and Dave Cox
In an Account Takeover (ATO), Cybercriminals exploit stolen login credentials to take over online accounts. Account takeovers can either target people within an organization, allowing hackers to steal sensitive information, or they can target customer accounts, enabling fraudulent transactions.
Given that ATO attacks have increased by 354% since 2023, a strong ATO prevention strategy is more important than ever in reducing risk for customers and businesses. This guide covers everything you need to know about detecting and preventing Account Takeover attacks.
What is an Account Takeover attack (ATO)?
ATO attacks can affect any organization with user-facing logins. Cybercriminals steal credentials through phishing, social engineering, mass data breaches, or purchases from the dark web. Once the attackers seize user credentials, they deploy bots to test them across various sites. After finding valid combinations, they can sell confirmed credentials or use them to commit fraud.
Account takeovers are particularly dangerous because they can go undetected for a long time. After all, without any active identity verification defenses, they look like valid sign-ins. Additionally, users might not notice unauthorized activities immediately, giving attackers plenty of time to exploit compromised accounts.
Cybercriminals are also constantly improving the sophistication of their bots and developing new attack strategies, making ATOs ever more challenging to detect.
Examples of ATO Consequences
Account takeovers can have various, far-reaching repercussions. Let’s cover some of the actions an attacker can take after a successful ATO.
Fraudulent transactions: A cybercriminal can use a stolen account to make unauthorized purchases or exploit the account for other illegal activities. For example, a compromised eCommerce account can be used to buy high-value items and ship them to an address where the hacker can claim them. The cybercriminal can then resell those items, often in legal marketplaces.
Data Theft: Access to an account can lead to the theft of personal information, which can then be sold or used for identity theft. Personal information like Social Security numbers, addresses, and bank details are highly valuable since they can be used to open new credit accounts and file for fraudulent tax refunds. Many users also reuse login credentials, so having one set of credentials allows hackers to carry out credential stuffing attacks and compromise more of their accounts.
Financial Theft: Attackers might directly steal money from a user’s bank accounts or use linked credit cards to make purchases. This can involve unauthorized wire transfers or maxing out credit limits, and these funds can’t always be recovered. Victims often face significant financial losses and a lengthy process to restore their credit.
Internal Phishing: Once inside an account, attackers can send phishing emails to contacts, posing as the account owner to spread the attack further. This type of attack can lead to widespread data breaches across an entire organization.
How do Account Takeovers Happen?
Understanding how account takeovers happen is the first step in preventing them. These are some of the most common techniques attackers use to steal credentials:
Phishing: Cybercriminals trick users into revealing their login credentials by sending them emails or DMs that look legitimate. These messages will link to a spoofed login page which will record the user’s password and username. Phishing attacks typically mimic trusted entities like banks or email providers, making it easy for users to mistake the requests as legitimate.
Malware: Malicious software installed on a device can capture keystrokes and send this information to the attacker. Attackers can filter these keystrokes to find login credentials. Malware can be delivered through email attachments or infected websites and downloads. Once installed, malware operates silently in the background, stealing information without the user’s knowledge.
Man-in-the-Middle Attacks: Attackers intercept communication between a user and a website to capture sensitive information. MITM attacks are particularly effective on unsecured public WI-FI networks. Using encrypted connections and VPNs can help protect against MitM attacks.
Credential Stuffing: Involves using large lists of stolen credentials to access accounts. Credential stuffing attacks are carried out with bots. What makes them effective is that if a hacker discovers even a small percentage of reused passwords in their dataset, they can achieve a succession of account takeovers.
Brute Force: This method involves systematically guessing passwords until the correct one is found. It’s most effective against accounts with weak passwords. Attackers use automated tools to test millions of password combinations quickly. Brute force attacks can be mitigated by having strong, unique passwords and limiting the number of login attempts possible in a time window.
How to Detect Account Takeover
Detecting an account takeover (ATO) early is crucial for minimizing its impact on your enterprise. Here are some key indicators and best practices for improving your identification processes:
Unusual activity is the first sign of a compromised account. Examples include fraud alerts or unusual charges on accounts. For instance, if your finance department notices unapproved transactions, this could signal an ATO. Regularly monitoring your accounts and setting up alerts for suspicious activities are essential practices. Using advanced analytics tools that identify anomalies in transaction patterns can help your security team quickly detect and respond to potential takeovers.
Multiple failed login attempts are another significant warning sign. This can indicate that someone is attempting to breach your systems through brute force or credential-stuffing attacks. For example, if your IT department detects a spike in failed logins, it could be an early indication of an ATO attempt. Implementing monitoring tools that track login attempts across your entire infrastructure and setting up alerts for repeated failures can enable your security team to act swiftly and prevent breaches.
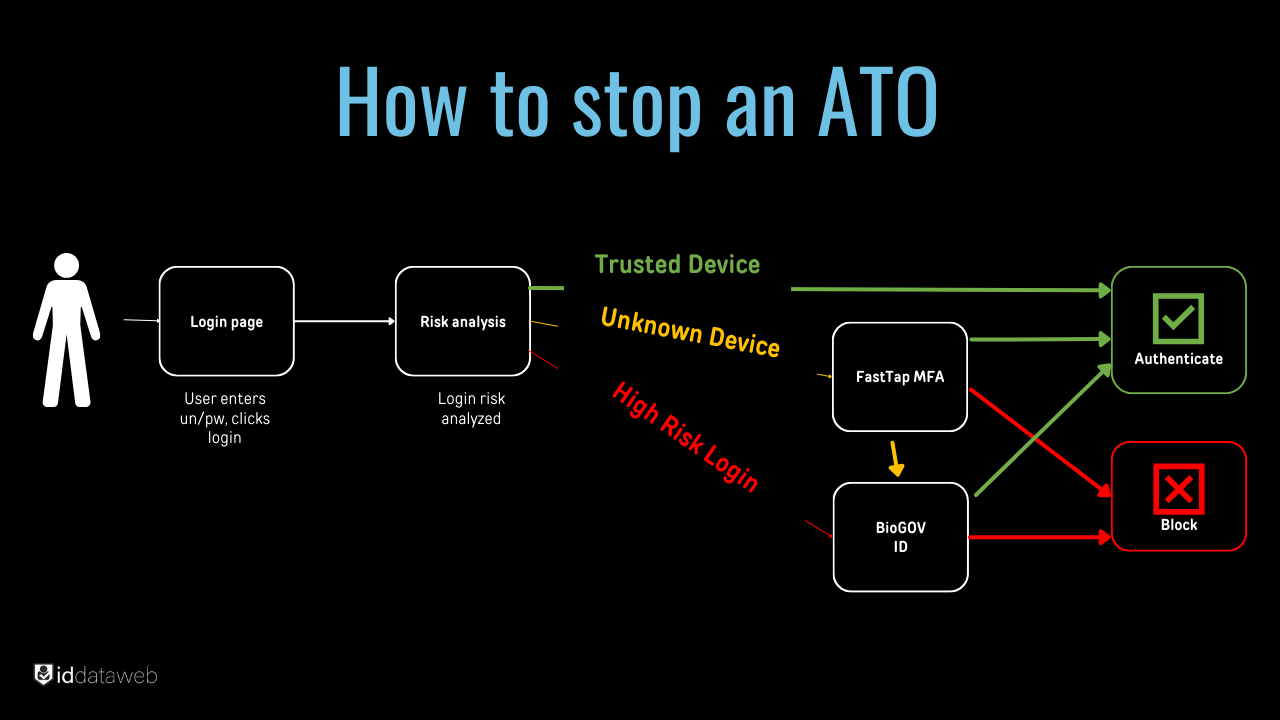
Logins from unfamiliar devices or locations are also red flags. For instance, if a login attempt is made in a country where your company has no operations, it should trigger an immediate review. Employing two-factor authentication (2FA) and maintaining a detailed log of login histories can ensure that only authorized users access accounts. This additional layer of security makes it significantly harder for attackers to gain access even if they have obtained valid credentials.
Sudden changes to account settings, such as updates to email addresses or passwords, can indicate a potential takeover. Attackers often change contact information to block the legitimate account owner from receiving security alerts. For example, if a user’s contact details are altered without proper authorization, it should raise an immediate alarm. Regularly auditing account changes and maintaining strict control over who can alter critical settings are vital. Implementing 2FA for these changes and setting up approval workflows for any modifications to internal accounts can further protect against unauthorized access.
Advanced ATO Prevention Strategies
Here are some additional strategies to prevent ATO:
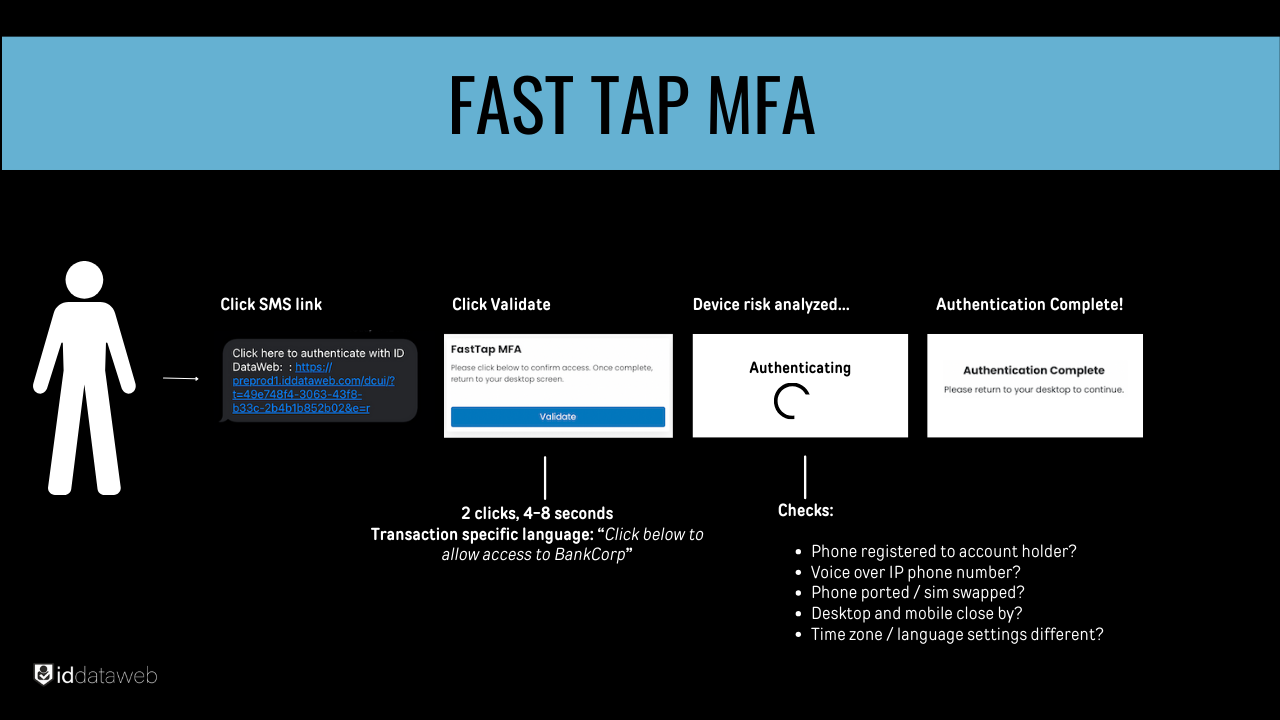
Multi-Factor Authentication (MFA) is one of the most effective ATO prevention strategies. Implementing MFA adds an extra layer of security beyond passwords. This could involve something the user knows (like a password), something they have (like a token or mobile device), or something they are (biometric data). For example, a financial institution requiring both a password and a fingerprint scan significantly reduces the risk of unauthorized access, as attackers would need multiple forms of verification to succeed.
Account Tracking Systems are essential for continuous monitoring of account activity. These systems can sandbox suspicious accounts for further investigation, preventing potential damage. For instance, if an e-commerce platform notices unusual purchasing patterns from an account, it can temporarily restrict access while conducting a deeper analysis. Real-time monitoring and anomaly detection tools can quickly identify and respond to potential threats, enhancing overall security.
AI-Based Detection systems are highly effective in identifying sophisticated ATO attempts and bot attacks. AI can analyze behavior patterns and flag anomalies that might indicate a security threat. For example, machine learning algorithms can detect unusual login times or locations and automatically initiate additional verification steps. These systems continuously improve by learning from new attack patterns and behaviors, providing an adaptive defense mechanism.
Web Application Firewalls (WAFs) offer another crucial layer of defense. A WAF protects web applications by filtering and monitoring HTTP traffic, blocking malicious traffic, and identifying credential stuffing or brute force attacks. For example, a WAF can inspect incoming traffic for known attack patterns and block suspicious requests before they reach your application. This helps prevent unauthorized access and protects sensitive data from being compromised.
Regular Security Audits are vital for maintaining robust security measures. Conducting regular audits helps identify vulnerabilities in your systems and processes, allowing you to address potential threats proactively. For instance, a comprehensive security audit should include penetration testing, vulnerability assessments, and compliance checks. These audits can uncover weaknesses that attackers might exploit, enabling you to fortify your defenses before a breach occurs.
Account Takeover Prevention with ID Dataweb
ID Dataweb offers advanced solutions to protect against account takeover (ATO) through robust identity verification, validation processes, and fraud analysis features. These solutions are designed to ensure seamless security without disrupting user experience.
Identity Verification is the cornerstone of preventing unauthorized access. ID Dataweb’s verification processes involve cross-referencing multiple personal data points to accurately confirm user identities. This includes:
- Name to Address: Ensures the provided name matches the recorded residential address.
- Name to Date of Birth: Confirms that the name aligns with the date of birth.
- Name to SSN: Verifies the name against the Social Security Number.
- Name to Phone: Checks the name against the phone number.
- SSN to Address: Matches the Social Security Number with the residential address.
- SSN to Date of Birth: Links the SSN to the correct date of birth.
- Address to Date of Birth: Ensures the address matches the date of birth.
- Address to Phone: Confirms the address aligns with the phone number.
These verification steps are crucial for establishing user legitimacy and significantly reducing the risk of ATO.
Identity Validation Signals to provide an additional layer of security, by delivering real-time validation that enhances the overall integrity of the verification process. These signals include:
- Allowed Location: Verifies if the login attempt originates from a permissible geographic location.
- Watchlist Check: Screens the identity against known watchlists to identify potential threats.
- Not Deceased: Ensures that the individual is not recorded as deceased, which could indicate identity theft.
- Residential Address: Confirms the address provided is a valid residential location.
- Safe Phone Type: Ensures the phone number provided is of a safe type, such as avoiding VOIP numbers often used in fraudulent activities.
ID Dataweb’s advanced identity verification solutions help prevent ATO by ensuring only authorized users gain access. But don’t just take our word for it—start a demo and see the value of ID Dataweb’s identity verification workflow for yourself.